My Domino server 10.0.1 FP8
when use starttls sending to the specific email domain ,
09:37:07.09 SSLEncodeClientHello> We offered SSL/TLS version TLS1.2 (0x0303)
Hi,Set config RouterFallbackNonTLS = 1 https://support.hcl-software.com/csm?id=kb_article&sysparm_article=KB0079251
SSL handshake error: 1C7Bh usually means that the other side tries to connect with a SSL/TLS Version that is not supported by your Server.
You might do as suggested by Rainer Brandl, but this will bring you a finding at the next Network Security Scan. Allowing unencrypted Connections is a Security Risk, what you need to do depends on the Security Policy of your Company. Maybe you accept it that Servers with weak encryption cannot connect to your Server, these are only a few. No major Provider works with less than TLS 1.2.
As a compromise, you might check if there is a Parameter SSL_DISABLE_TLS_10=1 is in your notes.ini.
Removing this Parameter would allow to connect with less secure TLS1.0 but still prohibit unencrypted connections.
Customers need to use StartTLS protocol to transmit emails, and only support 1.2 and 1.3
Next guess would be then, that the two Servers don't find a common Cipher.
I would suggest you increase the Loglevel with
DEBUG_SSL_ALL=3 SSL_TRACE_KEYFILEREAD=1
In the notes.ini an then search for "cipherspec" in the Log. Also check, which Ciphers are selected in the SSL Settings in the Server Document.
These two parameters have been added,
on this customer...
Checking keyfile certificates:
===============================================
But sending to other side ( example google ), it is no problem
Checking keyfile certificates:
As you can see, the receiving Server without Problem negotiates the ECDHE_RSA_WITH_AES_128_GCM_SHA256 Cipher.
Please check the Cipher Settings in your Server Document also contains
ECDHE_RSA_WITH_AES_256_GCM_SHA384
Maybe the Server that gives you trouble doesn't accept 128 Bit Ciphers.
jerome
January 18, 2024, 2:13pm
8
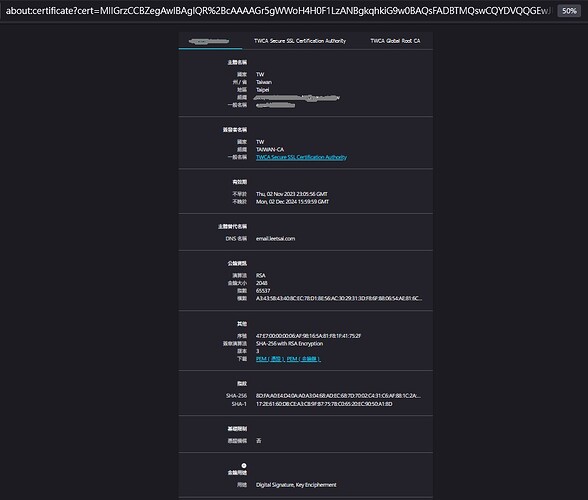
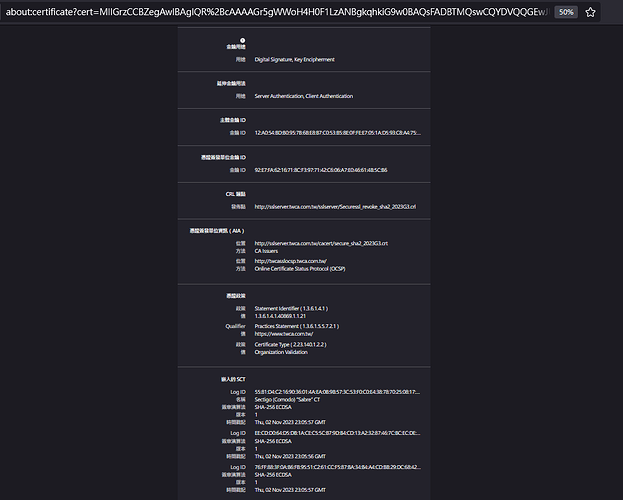
@Taiwan Jimmy Lu , have you check your ssl certificate? It must have extended "Server Authentication, Client Authentication", the "client authentication" is mandatory for starttls.
Yes, we have obtain a certificate for the client from a trusted CA ..
jerome
January 19, 2024, 11:27am
10
@Taiwan Jimmy Lu , just under your last section (the green arrow) check "Extended Key usage", you should have "Server authentication" AND "Client Authentication" (the green rectangle I do not have on you screen shot)
thank you for your response, the field have the value