I have a Nomad server (1.0.13 on Domino 12.0.2 FP5, 64-bit) running on Windows.
I now have a certificate issued to the server by our internal certificate authority in the US. It was created based on a CR generated by a TLS Credentials document in certstore.nsf.
The root certificate I have imported, and after processing it is marked by Certstore as valid.
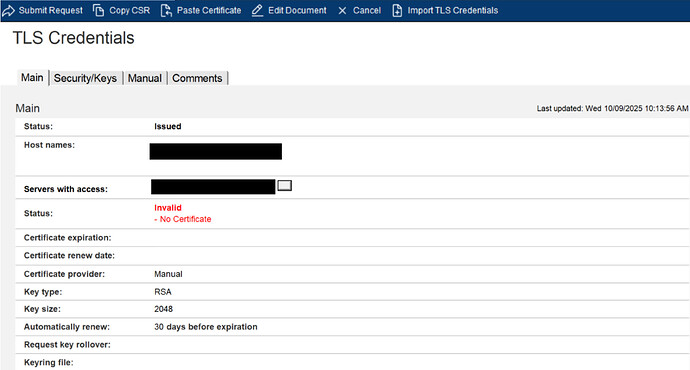
I then paste the certificate into the "paste" field on the "Manual" tab of the credentials doc, but after processing it shows as "Invalid", with an explanatory note "No Certificate". I get the same result whether I paste in just the leaf certificate or the leaf and root together.
What might I be doing wrong?
Thank you for pointing me at that article - I had not seen it before.
No, I did not follow that process. As described above, I pasted the contents of the .pem file in, and submitted them to the server.
I have now tried that alternative approach (importing, rather than pasting). The result, from importing the .pem, was a different error: "Error importing private key from PEM file". If I try instead to import the corresponding binary .cer I get "Cannot import without a private key".
The document does have a private key value stored, and I supposed that the corresponding public key would be included in the CSR on which the issued certificate is based.
Hi Andrew,
Sorry, I missed that part where you mentioned that the CSR is generated from the certstore. Can you confirm what is the version of the client you are using?
Client is 12.0.2 FP2, 32-bit (because we still have 32-bit clients in the environment, and there are a couple of issues between 64-bit Designer and 32-bit client).
@Shrikant Jamkhandi . do you have anything to add here? You were so helpful on my earlier, related question...
Hi Andrew,
Sorry to respond you late.
I assume that you generated CSR in the certstore.nsf and then CSR was sent to your internal CA for providing the certificate.
They have provided you the TLS cert for your Nomad server and you are having issue in the TLS credentials in the certstore. You also imported the CA root certs in the certstore.nsf under trusted root. Please let me know if I have understood this correctly?.
Follow the below steps:
Step 1: Import the internal CA trusted root in the certstore.nsf under Trusted Roots.
Step 2: Create new TLS Credentials document in the cerstore.nsf to generate a CSR. Certificate host name example "mynomad.notesdomtech.com" .
Step 3: Copy the CSR and save the CSR in a text file with .csr extension.
Step 4: Send the CSR to CA. CA will issue TLS certificate and TLS certificate may contain intermediate along with root certifier. In this example there is only Root.
Step 5: Merge all certificates ( server cert, intermediate and root) in a single file. You can use command prompt "Type" command to merge it. In this example there is no intermediate. It has only root.
type server.crt root.crt >final.pem
Step 6: Copy and paste the content of the above resulting file in the certsore.nsf using the "Paste Certificate" button.
Step 7: In the Security/Keys tab, under "Trusted Roots" select your internal root certifier.
Step 8: Click on Submit Request button. In few second the TLS certificate should be active.
I have made a short video on this for your reference.
Thank you
Regards
Shrikant J
Thank you, Shrikant.
What you recommend is exactly what I did. The result is a status of "Invalid" and an explanatory message "No Certificate".
Can you identify why it says that? I am looking at the certificate in the credentials document...
AB
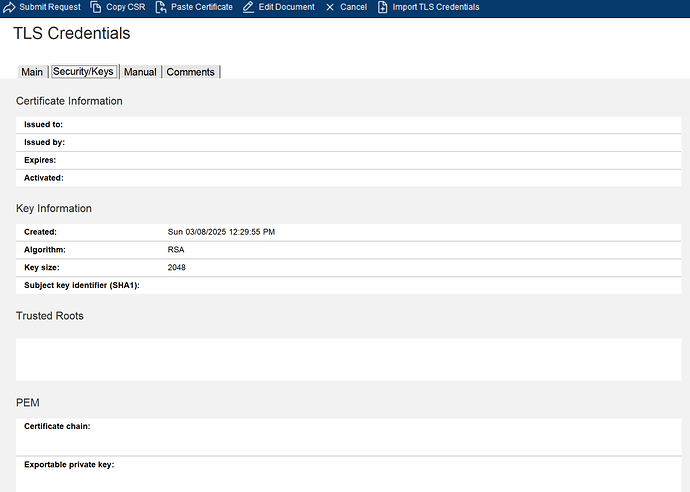
Hi Andrew, can you share the screen shot of the TLS document with error displayed also screen shot of the "Security/Keys" tab.
You can mask the information which is not required. Also let me know if there is a HCL support case opened we can work on it, as we may require to collect data
Thank you
Regards
Shrikant J
Hi @Shrikant
I’m back. Sorry to leave previously without answering you. Evidently I got distracted, but the problem then turned out to be that I had requested a 4096-bit certificate, but what I got back was based on a 2048-bit root. When I re-requested a 2048-bit certificate all was well.
But now…
The Domino server name (although not the hostname) has changed, so we need to start again. Learning from last time, I requested a 2048-bit certificate, which I have now received.
On pasting in the PEM and submitting it to Certmgr, I get the same message as before: “No Certificate”,
Here are the screenshots you requested earlier:
Hello Andrew,
When you open the .pem file in notepad or notepad ++, how many certificate you see in the file does it contain only server certificate and private key ?.
PEM file shows each certs starting with -----BEGIN CERTIFICATE----- & ends with -----END CERTIFICATE-----
If this file includes example 3 certificates and a private key then it should contain 4 number of BEGIN and END in the file.
Thank you
Regards
Shrikant J
Hi Shrikant
The PEM contains three certificates - a leaf (the specific server), an OU and the trusted root certifier, each bookended with -----BEGIN CERTIFICATE----- and -----END CERTIFICATE-----,
Importing and submitting the trusted root alone into a “Trusted Root” document in certstore works, but submitting the full certificate chain even after that continues to give me “No Certificate”.
I have two such PEMs, in fact, one for each of two servers. One worked immediately, but the other not. The root and OU cerficates are identical across the two files, as are all the headers, with the exception of course of the common name of the server certified. The hex string for the leaf certificate of the working one is somewhat longer (2044 characters) than that for the failing one (1662 characters). Is that a clue? Should I expect them to be the same length?
A solution found, of sorts.
Although the TLS Credentials document in certstore.nsf specified 2048-bit RSA, the actual .CSR generated apparently demanded a 4096-bit certificate. This was apparent only in the certificate generation software used by the certificate issuer.
Once I deleted that specification, created a new one from scratch and sent a new .csr based on that, the certificate returned worked.